With today’s technology, one of the well-known methods in tackling any computationally puzzling task is to leverage the untapped processing power of multiple endpoints. Well, that’s the idea behind a botnet: a comprehensive collection of malware-infected computers and servers which jointly serve under remote servers to perform malicious entities.
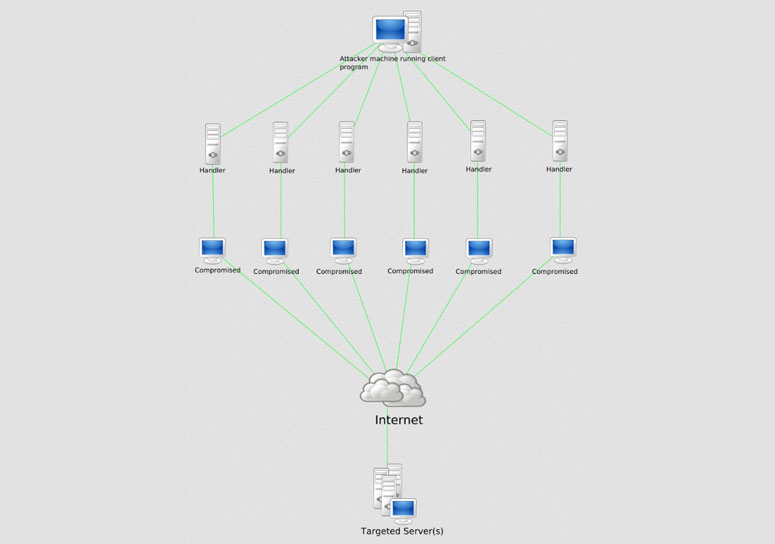
Once the malware affects the computers, the bots will then link back to remotely command and control (C&C) the compromised system to perform malicious acts. Additionally, bonnets can be used in various tasks like distributed denial of service, collecting sensitive data, and spam marketing.
In the old days, botnet existence used HTTP or IRC protocols to contact the infected systems. However, system users would block the communication through network security services. A good example is the Firefox web browser that uses a web-blocker command and control to block communication from botnet-affected systems.
Today, the advancement in technology is lethal as the number of botnets has proliferated. Their existence is more sophisticated, reaching more targets, anti-detected, advanced attack techniques, and infiltration. Therefore, you need to be more exposed to botnet detection tools and techniques.
This article gives you more knowledge about botnet detection, techniques, behavior analysis, and how vital are botnet detection tools.
How to search for bots on your network
Before searching for botnets on your systems, there might be some initial signs and symptoms. After botnet infiltration, the compromised system will begin manifesting some problems like executing its commands. By getting to know these signs and symptoms, you can help in early botnet detection. Let’s have a look at some of the initial signs and symptoms of botnet detection.
Initial signs and symptoms
- Generating internet ray chat (IRC) traffic through a specific range of ports
- Developing simple mail transfer protocol (SMTP) traffic/e-mails
- Linking to establish command and control (C&C) servers for instructions
- Creating simultaneous identical domain name system (DNS) request
- Compromising the workstation performance/ internet access
The listed issues above will typically manifest on any level, whether individual, affected workstation, or the network as a whole. However, network management has different botnet detection techniques that are usable at any level. They include:
Botnet detection at the endpoint
The endpoint technique can diagnose host-based botnet detection with an antiviral solution. It is possible to detect the bots because most of the infiltration will always happen through malware. Sometimes the antiviral technology may fail as a result of outdated signatures. That leads to antivirus technology failing to spot any infection. It is upon the administrators to look out for new issues.
When running a host-based botnet detection, it will involve non intentional performances like rootkit installations, sudden changes to the window host file, and Pop-ups while browsing through HTTP protocol. Additionally, you might find out that the default DNS servers are modified. Such symptoms and signs signal that the traffic is miss directed to places where it is not designed to go.
Botnet detection on the network
Network-based botnet detection is more complex. But users can use different approaches and among the many is the detection and monitoring of the IRC traffic. Most companies and individuals already use the technique in their network.
In IRC, traffic sent is unencrypted, which means a packet sniffer can identify the keywords. The bots can take advantage of identified ports, with the default port being 6667. Remember, all ports range from (6660-6669 and 7000).
When multiple endpoints are simultaneously and suddenly accessing one or more external sites. It is a clear sign that the botnet-driven (DDOS) is launching an attack from your network. A similar situation will happen when there is mass outbound traffic through the SMTP. It will then indicate spam-mailing has an issue. Therefore, it is essential to include the rules for any symptoms on your network-based security tools to tune them for botnet detection.
Botnet detection through honeypot
Network security gurus may consider creating a false infiltration opportunity to check whether it will indeed be infiltrated. And if injected, how will the process happen? There are many free, open-source intrusion detection solutions where users can receive a list of botnet recognition signatures. Always try getting any attempt to connect to known c&c servers.
Botnet detection categories
There are two categories of botnet detection, including Behavioral analysis and statistical analysis. The difference in both is that the statistical analysis is fast, simplistic, and resource-friendly, while, on the other hand, behavioral analyses are thorough and resource-intensive.
Behavioral analysis
It is virtually an essential approach in botnet detection. For example, a C&C server will issue blanket orders for bots to perform a specific action. That’s generating network activities enormously from a single point at a time.
In the analysis, the average time interval between the endpoint that connects to a different outbound server will be too low for the botnets, for no human is controlling the network activity. More failed connection attempts will be registered, and the majority will instead use numerical IP addresses than server names.
However, the P2P management architecture makes it harder for botnet detection. The new advancement works under a decentralized technology. It, therefore, means it has no central command and control servers. For such botnets, it isn’t easy to detect in early levels but can also be eliminated.
Statistical analysis
The technique is your first line of defense and will be of a higher match to malware signatures or any executable or C&C connections. Unfortunately, the statistical methods are no longer strong enough to follow rapidly sophisticated botnet managers.
Botnet tools and future botnet detection
Despite the significant evolution in botnets, there are better tools to detect and eradicate the bots. The new open-source solutions and more advanced integrated security intelligence are on offer in:
- Identifying the network origin
- Determining when the network activity is unusual
- Analyzing the nature and impact of the bots
- Eliminating, limiting, and quarantine local bots
The solution to botnets is even getting much better, faster, and wiser. It is all happening in various ways where some are human-centric, tech-centric and some combining both.
Conclusion
Employing machine learning techniques will significantly alleviate the problem of botnets in your network, workstations, or systems. There is more in advanced technology that is yet to open up new avenues of solving the issues. Some of the future enhancements will include things like the IRC traffic classification engine.


Comment Policy
Your words are your own, so be nice and helpful if you can. Please, only use your REAL NAME, not your business name or keywords. Using business name or keywords instead of your real name will lead to the comment being deleted. Anonymous commenting is not allowed either. Limit the amount of links submitted in your comment. We accept clean XHTML in comments, but don't overdo it please. You can wrap code in [lang-name][/lang-name] tags.